With Santa away, Wombley Cube and Alabaster Snowball have each tried to lead. Surely they won’t mess up the naughty and nice list…

Curling
The first character we see is Bow Ninecandle, who is super enthusiastic about curling.
Curling Silver Solution
Curling Gold Solution
We are given two hints.
- Take a look at cURL’s “–path-as-is” option; it controls a default behavior that you may not expect!
- The official cURL man page has tons of useful information on how to use cURL.
The challenge is worked inside of a terminal environment. We are given a series of objectives to achieve using curl commands, as they are achieved we are advanced to the next round.
Curling Silver Solutions
- Unlike the defined standards of a curling sheet, embedded devices often have web servers on non-standard ports. Use curl to retrieve the web page on host “curlingfun” port 8080.
- Command
curl http://curlingfun:8080
- Response:
- You have successfully accessed the site on port 8080!
- Command
- Embedded devices often use self-signed certificates, where your browser will not trust the certificate presented. Use curl to retrieve the TLS-protected web page at https://curlingfun:9090/
- Command
curl https://curlingfun:9090 --insecure --include
- Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Sat, 14 Dec 2024 01:14:44 GMT
Content-Type: text/plain;charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
Custom-Header: You have found the custom header!
You have successfully bypassed the self-signed certificate warning!
Subsequent requests will continue to require "--insecure", or "-k" for short.
- Command
- Working with APIs and embedded devices often requires making HTTP POST requests. Use curl to send a request to https://curlingfun:9090/ with the parameter “skip” set to the value “alabaster”, declaring Alabaster as the team captain.
- Command
curl --data "skip=alabaster" https://curlingfun:9090 --insecure
- Response
You have successfully made a POST request!
- Command
- Working with APIs and embedded devices often requires maintaining session state by passing a cookie. Use curl to send a request to https://curlingfun:9090/ with a cookie called “end” with the value “3”, indicating we’re on the third end of the curling match.
- At this stage we can complete the Silver medal by submitting the following command.
curl --data "skip=alabaster" https://curlingfun:9090 --insecure --cookie "end=3" --path-as-is https://curlingfun:9090/../../etc/hacks --header "Stone: Granite")- Doing so will unlock some dialog from the elf.

- Or continuing as intended, the command is…
curl https://curlingfun:9090 --insecure --cookie "end=3"
- Response
You have successfully set a cookie!
- At this stage we can complete the Silver medal by submitting the following command.
- Working with APIs and embedded devices sometimes requires working with raw HTTP headers. Use curl to view the HTTP headers returned by a request to https://curlingfun:9090/
- Command
curl https://curlingfun:9090 --insecure -v
- Response
- Headers are displayed, followed by:
You have successfully bypassed the self-signed certificate warning!
Subsequent requests will continue to require "--insecure", or "-k" for short.
If you need help, please remember to run "hint" for a hint!
Connection #0 to host curlingfun left intact
- Headers are displayed, followed by:
- Command
- Working with APIs and embedded devices sometimes requires working with custom HTTP headers. Use curl to send a request to https://curlingfun:9090/ with an HTTP header called “Stone” and the value “Granite”.
- Command
curl https://curlingfun:9090 --insecure --header "Stone: Granite"
- Response
You have successfully set a custom HTTP header!
- Command
- curl will modify your URL unless you tell it not to. For example, use curl to retrieve the following URL containing special characters: https://curlingfun:9090/../../etc/hacks
- Command
curl https://curlingfun:9090/../../etc/hacks --insecure --path-as-is
- Response
You have successfully utilized --path-as-is to send a raw path!
- Command
- Silver medal achieved!
Curling Gold Solution
Gold is similar but with a twist. It’s not ‘hidden’ but it’s in a place we might not look otherwise.
- Inspecting the terminal environment with an
lscommand we see there is a file called HARD-MODE.txt. This file contains the Gold challenge.- Command to inspect the file contents
cat ./HARD-MODE.txt
- File contents
Prefer to skip ahead without guidance? Use curl to craft a request meeting these requirements:
HTTP POST request to https://curlingfun:9090/
Parameter "skip" set to "bow"
Cookie "end" set to "10"
Header "Hack" set to "12ft"
- Command to inspect the file contents
- To complete the Gold challenge in a single step we can issue this command.
curl -X POST https://curlingfun:9090 --data "skip=bow" --cookie "end=10" --header "Hack: 12ft" --insecure --path-as-is https://curlingfun:9090/../../etc/button --path-as-is https://curlingfun:9090/GoodSportsmanship -L
- Otherwise we can continue step by step
- Command 1
curl -X POST https://curlingfun:9090 --data "skip=bow" --cookie "end=10" --header "Hack: 12ft" --insecure
- Response
Excellent! Now, use curl to access this URL: https://curlingfun:9090/../../etc/button
- Command 2
curl https://curlingfun:9090/../../etc/button --path-as-is --insecure
- Response
Great! Finally, use curl to access the page that this URL redirects to: https://curlingfun:9090/GoodSportsmanship
- Command 3
curl https://curlingfun:9090/GoodSportsmanship -L --insecure
- Response
Excellent work, you have solved hard mode! You may close this terminal once HHC grants your achievement.
- Command 1
- The gets us the Gold curling trophy. Additionally, we are awarded with excellent foreshadowing!
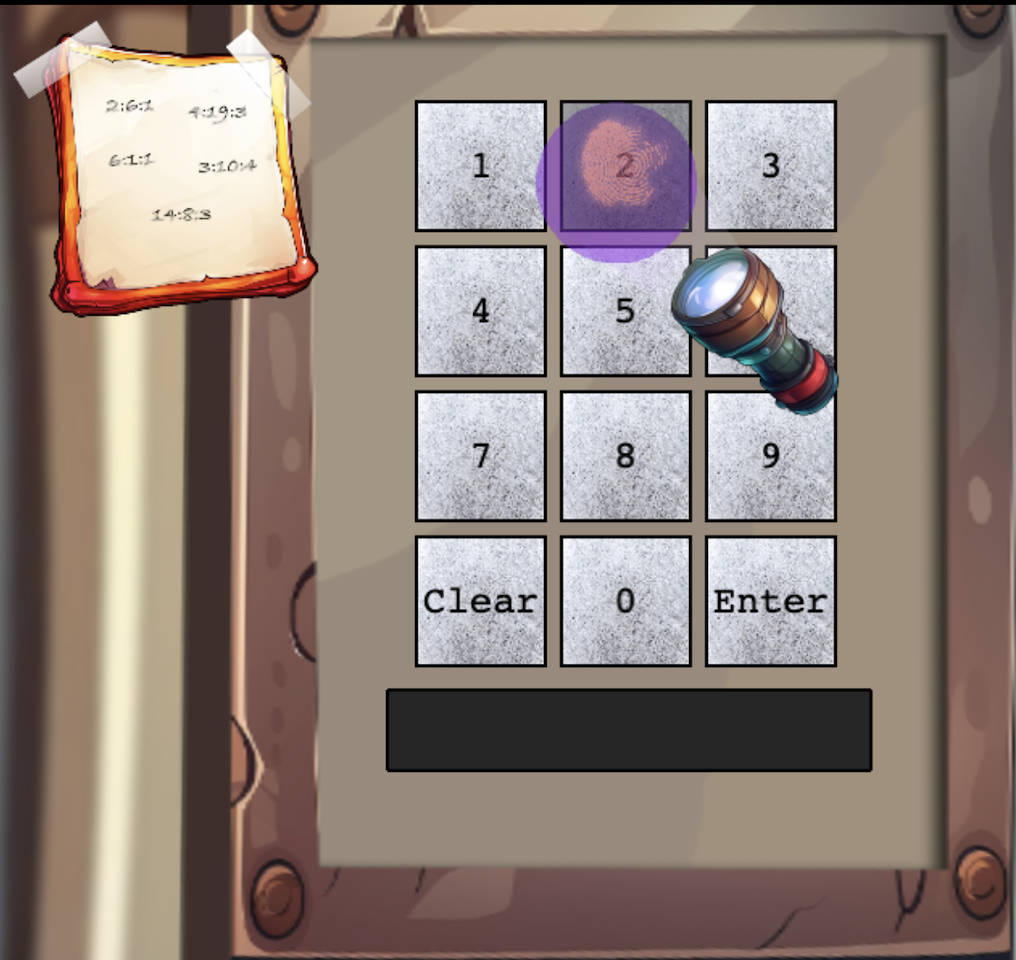
Frosty Keypad
Morcel Nougat needs our help to bypass a keypad they’ve lost access to.
We are given three clues
- Hmmmm. I know I have seen Santa and the other elves use this keypad. I wonder what it contains. I bet whatever is in there is a National Treasure!
- See if you can find a copy of that book everyone seems to be reading these days. I thought I saw somebody drop one close by…
- Well this is puzzling. I wonder if Santa has a separate code. Bet that would cast some light on the problem. I know this is a stretch…but…what if you had one of those fancy UV lights to look at the fingerprints on the keypad? That might at least limit the possible digits being used…
Sounds like first we need to find a flashlight and a book. There is websocket traffic that will tell us where any items of interest are located which makes them easy to find, but just wandering around by the keypad challenge will get you the items as well quickly enough. This is a screencap taken using Burp Suite of that traffic.
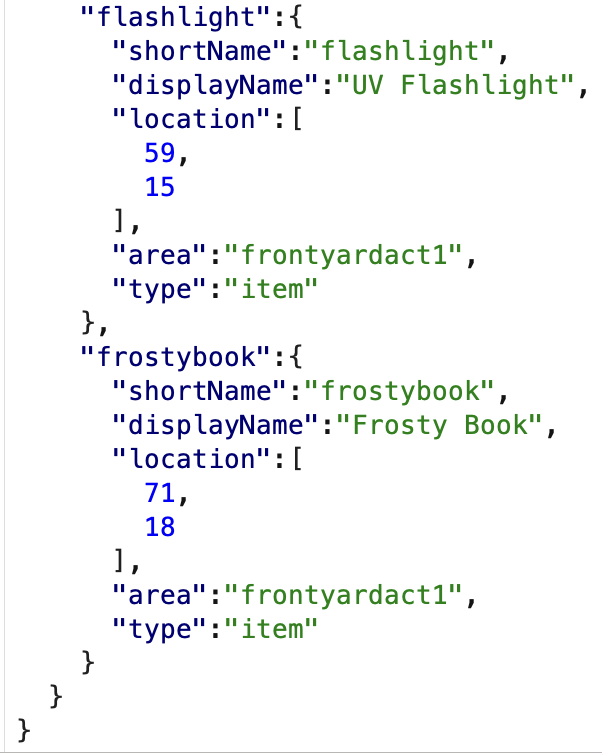
We can see our character location as well in this traffic and zero in on locations that way.

Now that we have the required items, we can begin the challenge. It’s possible to brute force this challenge without the flashlight or book, but it’s faster with the flashlight and solving the book cipher is more interesting than brute forcing it anyway.
Silver is a Book Cipher
Looking at the keypad itself we see that there is a note taped to the corner with 5 groups of numbers.

Examination of the keypad shows us that the code is 5 (or less) numbers long. It seems likely the note is an encoded version of one of the passcodes we need.
Given the number grouping, one of the numbers has to be ‘letter’. One is very likely to be ‘page’. The other will be sentence, word, or paragraph (it turns out that word is correct).
The book itself has the poem “A Visit from St. Nicholas” by Clement Clarke Moore.

- The numbers on the note are formatted A:B:C.
- There are 14 pages. The middle number (B) on the top right is 19, so the middle number can’t be pages.
- The largest number in another place is the (A) placement of the bottom number and that’s 14…so let’s assume the first spot is pages.
- A bit of experimenting with combinations shows us that “Page:Word:Letter” makes the most sense.
- Using that we can assemble the code: The word is SANTA. So we just..key…in…oh.
- Luckily it’s not too much of a stretch to get from SANTA to the 5 digit code we need.
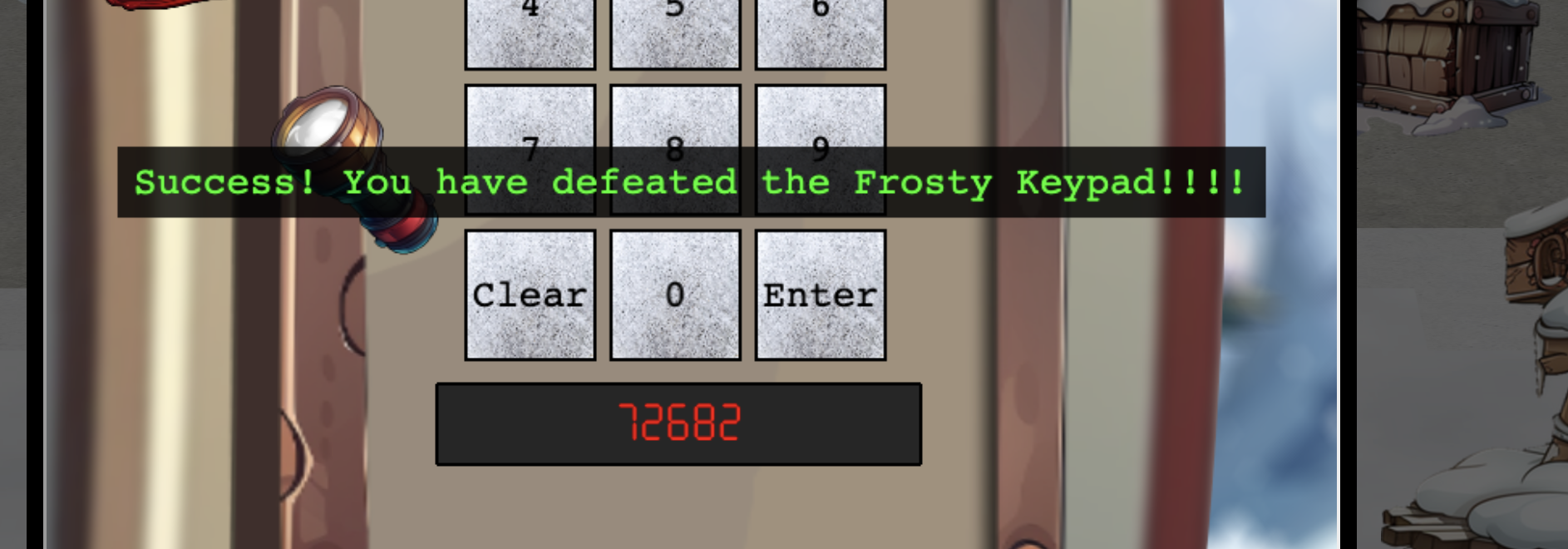
- The code for silver is 72682
Gold requires us to brute force the code
Using the UV flashlight we find that 2, 6, 8, and 7 are used frequently.
A couple assumptions make this step go faster.
- We can assume the code is 5 or less numbers long using some combination of 2,6,8, and 7 with one number being used twice.
- SANS probably doesn’t want everyone brute forcing this thing for hours, so the code that we need to brute force probably starts with 2. It’s reasonable to start there anyway, and that reduces the initial number of possibilities to 256 vs. 1024. (this turns out to be correct and every time I tried this I got in almost immediately).
Also during this challenge I ran across this informational tidbit:{"error":"The data you've provided seems to have gone on a whimsical adventure, losing all sense of order and coherence!"}
Wouldn’t be the first time web server. My apologies.
I used Burp to brute force the code.
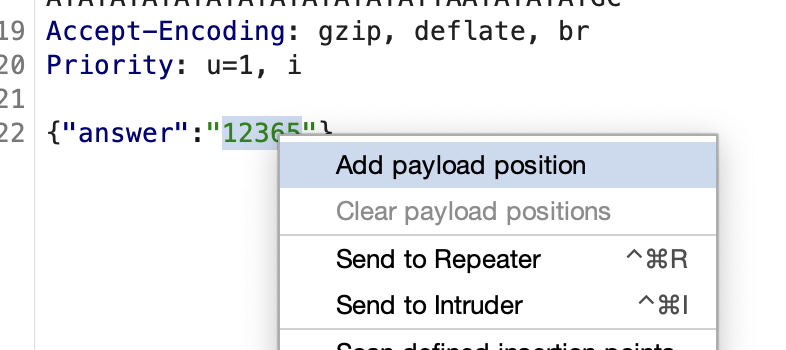
- First we intercept an attempt to guess the combination and forward that to Burp Intruder.
- Set the combination as the payload by highlighting the value and selecting ‘add payload position’.
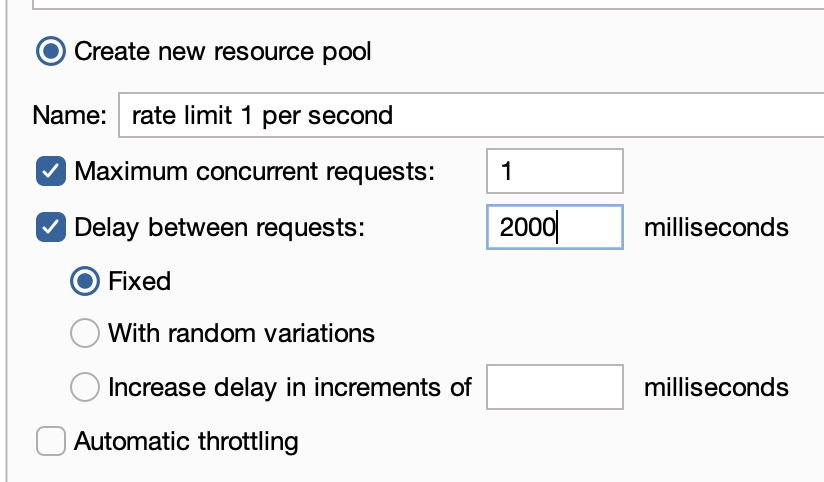
- Configure the payload
- Set the type to Brute Force.
- Set the payload to our character set of 2687
- Change the minimum and maximum length to 4
- Under ‘payload processing’ select ‘add’ and create a prefix rule. Set that value to 2.
- This will brute force all 5 digit combinations of our character set starting with the number 2.
- Almost immediately we see errors due to rate limiting. The simplest way to get around that is to slow down our requests.
- Kick off the request again and we should quickly get our solution. The code we need for Gold is 22682.
We are rewarded scraps of paper and an inspirational message.

On the Cutting Edge
This challenge has no trophy associated with it, but ties together ‘Frosty Keypad’ and ‘Hardware Hacking I’. Jewel Loggins gives us the background over at the Hardware Hacking challenge station: “We used to have a note with the serial settings, but apparently, one of Wombley’s elves shredded it! You might want to check with Morcel Nougat—he might have a way to recover it.” More on that after we complete this challenge.
Cutting edge has no trophy, but there is still an ‘easy’ and ‘hard’ level solution here. The easy solution is reassembling the shredded document. For the hard solution, we reassemble a message hidden in the metadata.
We are given a “hint” that tells us how to perform the assembly. Actually it gives us everything we need. Sweet.

Reassembling the image
- The link in the ‘shredded pieces of paper’ item downloads a zip file. Extracting this gives us 1000 very narrow image files.
- The script linked to in the hint requires very little to make it work. Fill in the file name in the script and run it.
- The results have a few pieces flipped. It’s easy enough to work out from the original on the left. Reassembled the full instructions are on the right.
Reassembling the metadata
We have what we need to move on to the hardware hacking challenge, but examining the image files closer it seems there is more here.
- We can extract the exif data for examination.
exiftool ./slices/* > exif.txt
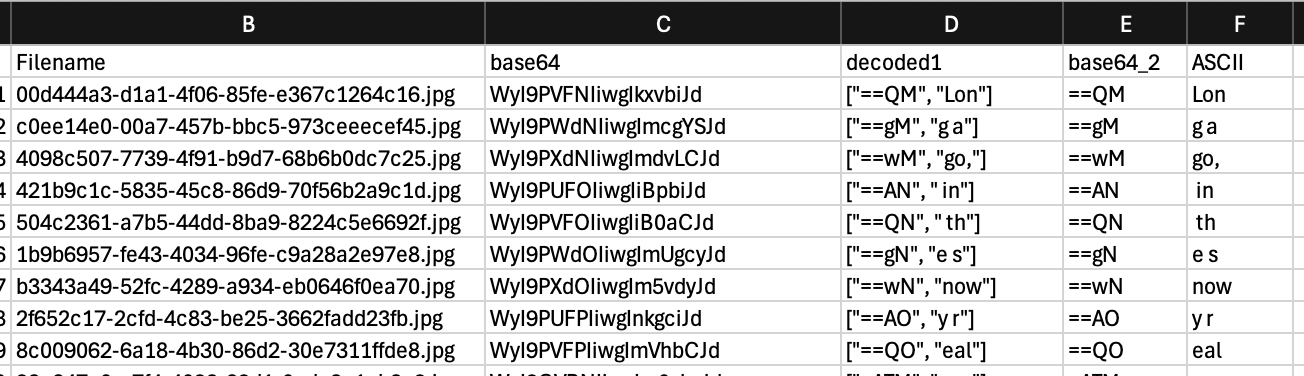
- Included in the output is a base64 string under ‘user comment’.
User Comment : WyI9VURPIiwgIiBmciJd- decoded, this is [“=UzN”, “s f”]
- The first portion is also base64, but I wasn’t able to find anything in that decoded output. Assembling the second portion from each file gives us the message we’re after.
- The metadata message isn’t scrambled like the images are, which makes this much simpler. If we extract the metadata from each image in numerical order we can reassemble the message. My extraction looks like this in progress.
- The reassembled message was partially garbled in a few places and I corrected a few errors manually. This is what I ended up with…
Long ago, in the snowy realm of the North Pole (not too far away if you're a reindeer), there existed a magical land ruled by a mysterious figure known as the Great Claus. Two spirited elves, Twinkle and Jangle, roamed this frosty kingdom, defending it from the perils of holiday cheerlessness. Twinkle, sporting a bright red helmet-shaped hat that tilted just so, was quick-witted and even quicker with a snowball. Jangle, a bit taller, wore a green scarf that drooped like a sleepy reindeer's ears. Together, they were the Mistletoe Knights, the protectors of the magical land and the keepers of Claus'e. One festive morning, the Great Claus summoned them for a critical quest. 'Twinkle, Jangle, the time has come,' he announced with a voice that rumbled like thunder across the ice plains. 'The fabled Never-Melting Snowflake, a relic that grants one wish, lies hidden beyond the Peppermint Expanse. Retrieve it, and all marshmallow supplies will be secured!'
Armed with Jangle's ha' map (created with crayon and a lot of optimism), the duo set off aboard their toboggan, the Frostwing. However, the map led them in endless loops around the Reindeer Academy, much to the amusement of trainee reindeer perfecting their aerial maneuvers. Blitzen eventually intercepted them, chuckling, 'Lost, fellas?
The snowflake isn't here at Enchanted Peppermint Grove!' Twinkle facepalmed as Jangle pretended to adjust his map. With Blitzen's directions, they zoomed off again, this time on the right course. The Peppermint Grove was alive with its usual enchantments-candy cane trees swayed and sang ancient ballads of epic sleigh battles and the triumphs of Claus...?? 'y ca'adro' ?? Twinkle and Jangle joined the peppermint choir, their voices harmonizing with the festive tune. Hours later, the duo stumbled upon a hidden cave guarded by giant gumdrop sentinels (luckily on their lunch break). Inside, the air shimmered with Claus' magic and they saw the Never-Melting Snowflake, glistening on a pedestal of ice.
Twinkle's voice range out - We've found it, Jangle! The key, marshmallows! As Twinkle reached for the snowflake, a voice boomed from the cave walls, 'One wish, you have. Choose wisely or face the egg-nog of regret.' Without hesitation, Jangle exclaimed, 'An endless supply of marshmallows for our cocoa!' The snowflake glowed, and with a burst of magic, marshmallows poured down, covering the cave in a fluffy, sweet avalanche. Back at the workshop, the elves were hailed as heroes-the Marshmallow Knights of Claus. They spent the rest of the season crafting new cocoa recipes and sharing their bounty with all. And so, under the twinkling stars of the northern skies, Twinkle and Jangle continued their adventures, their mugs full of cocoa, their hearts full of joy, and their days full of magic. For in the North Pole, every quest was a chance for festive fun, and every snowflake was a promise of more marshmallows to come.
Hardware Hacking I
Jewel Loggins needs our help getting into a tool called “Santa’s Little Helper” that they’ve lost access to. Step one is to get the UART interface working again.
Hardware Hacking I Silver
Hardware Hacking I Gold
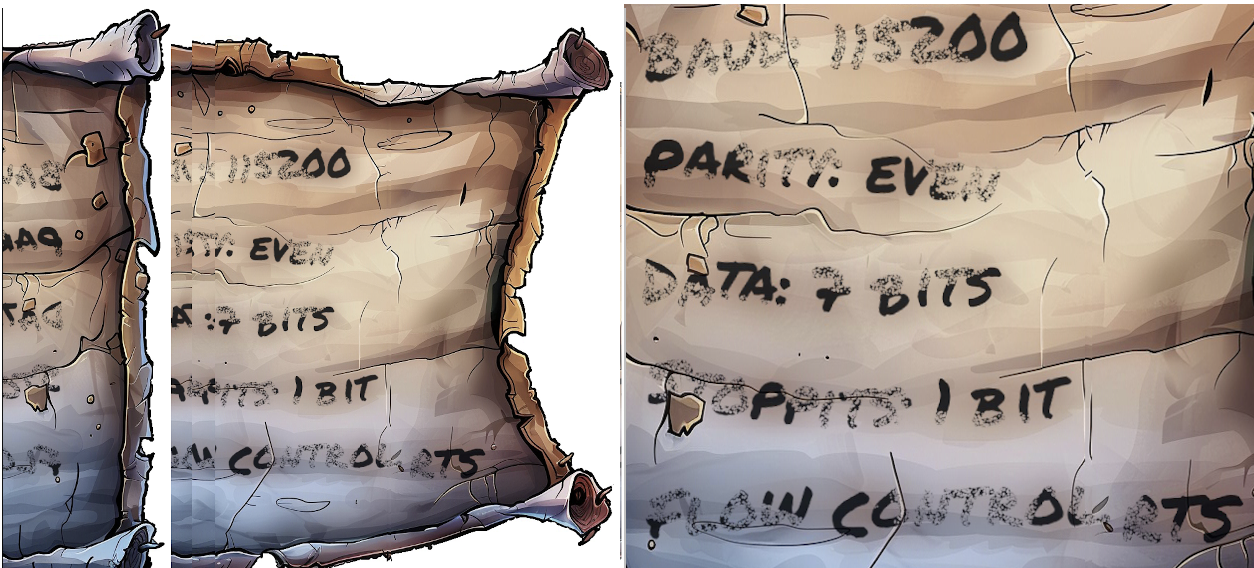
We have these settings from the previous challenge “The Cutting Edge”.
- Baud: 115200
- Parity: Even
- Data: 7 Bits
- Stop Bits: 1 Bit
- Flow Control: RTS
This is another challenge with fun stuff in the code.
// Power on fail phrases
const tryagainphrases = [
"Level incomplete! Keep playing!",
"Insert coin to continue your quest!",
"Continue? Time's running out!",
"You haven't beaten the high score yet!",
"Mission not accomplished! Retry?",
"Game over? Not yet, give it another shot!",
"The Force is not yet strong with this one.",
"You haven't completed your Jedi training.",
"Mission incomplete. The Rebellion still needs you.",
"The Death Star plans are still out of reach.",
"Your journey to the Dark Side is not over.",
"The Force is calling, but you haven't answered.",
"The Matrix still holds you, Neo.",
"You haven't broken free of the simulation yet.",
"Red pill taken, but the truth is not revealed.",
"The code is still incomplete. Keep hacking.",
"The Architect awaits your next move.",
"Reality is still an illusion. Persist.",
"Objective not complete. The city still needs you.",
"Neural link still active. Dive deeper.",
"Hack incomplete. Keep infiltrating.",
"You're still a ghost in the machine.",
"Cyber mission not finished. Keep running.",
"The grid still controls you. Break free.",
"Mission to Mars not yet completed.",
"Stardate update: Task unfinished.",
"You haven't reached the final frontier.",
"The galaxy awaits your return.",
"Your voyage is incomplete. Keep exploring.",
"Space mission still ongoing. Continue the adventure.",
"Mission not complete, soldier. Keep fighting!",
"You haven't saved the day yet.",
"The hero's journey is unfinished.",
"The battle is still raging. Don't give up.",
"You haven't defeated the villain yet.",
"Keep going, the action isn't over."
];Silver
We have all of the settings we need for the UART from the previous challenge except for the power setting.
5v has…consequences, so we’ll need to use 3v.

The voltage setting is done on the USB module in the bottom right of the screen and will need to be flipped from 5v to 3v by clicking on it.


We’ll also need to wire it up correctly. The important thing here is to make sure the Rx and Tx wires are swapped.
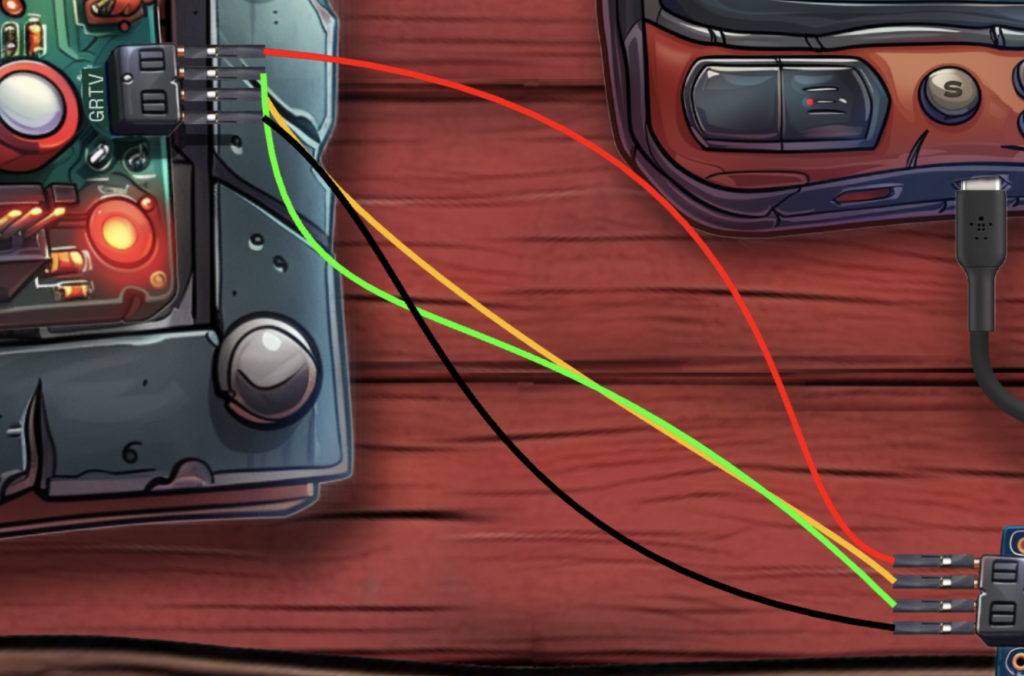
Incorrect UART settings result in an error message. Correct settings give us the Silver achievement.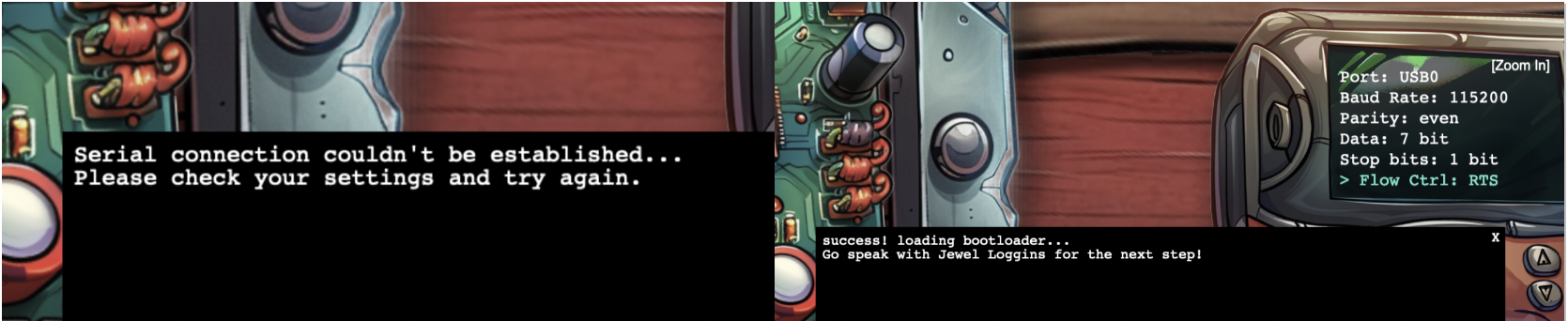
Gold
Jewel Loggins tells us what we’ll need to do for Gold.
Essentially, we’ll need to perform the same steps we did for silver, but we’ll need to do it without any of the pointing and clicking we did to configure the hardware earlier.
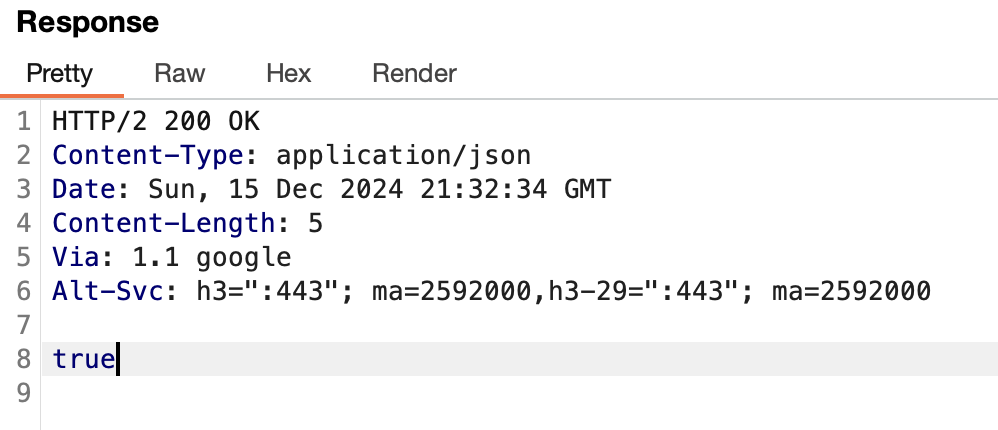
- Capturing and replaying the POST request using Burp Suite is easy enough, but at first we only get a response of “true”.
- Examining the .js code we find information about a vulnerable API version that may still be active.
// Word on the wire is that some resourceful elves managed to brute-force their way in through the v1 API.
// We have since updated the API to v2 and v1 "should" be removed by now.
// const url = new URL(`${window.location.protocol}//${window.location.hostname}:${window.location.port}/api/v1/complete`);
const url = new URL(`${window.location.protocol}//${window.location.hostname}:${window.location.port}/api/v2/complete`);
- To account for that, we update the API referenced in our POST request.
- This POST request is the final solution.
- Depending on exactly how we trigger the event we may see a new button appear by the UART.

- We can now access the console, so on to Hardware Hacking 2.
Hardware Hacking II
Now that we have the UART working, we can work on getting the Santa’s Little Helper app working.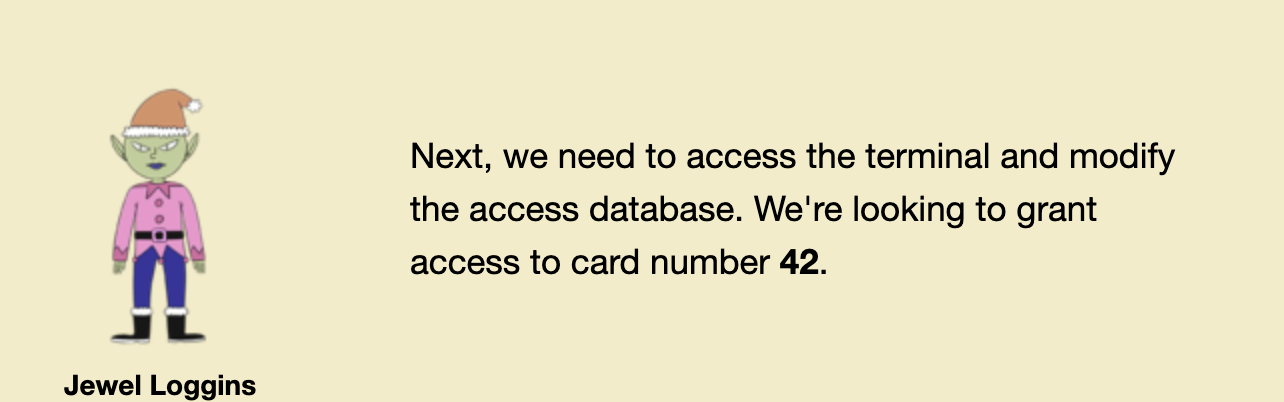
We are given 2 hints.
- I seem to remember there being a handy HMAC generator included in CyberChef.
- It is so important to keep sensitive data like passwords secure. Often times, when typing passwords into a CLI (Command Line Interface) they get added to log files and other easy to access locations. It makes it trivial to step back in history and identify the password.
Clicking on the console we are presented two options.
U-Boot is an open source bootloader with a cute submarine logo.
https://en.wikipedia.org/wiki/Das_U-Boot
We don’t need to interact with that directly for the challenge…we can do everything from option 1.
Hardware Hacking II Silver
- Entering option one we are presented with the Santa’s Little Helper (SLH) console.
- A quick look at the console history gives us what appear to be the credentials needed to provision the required access.
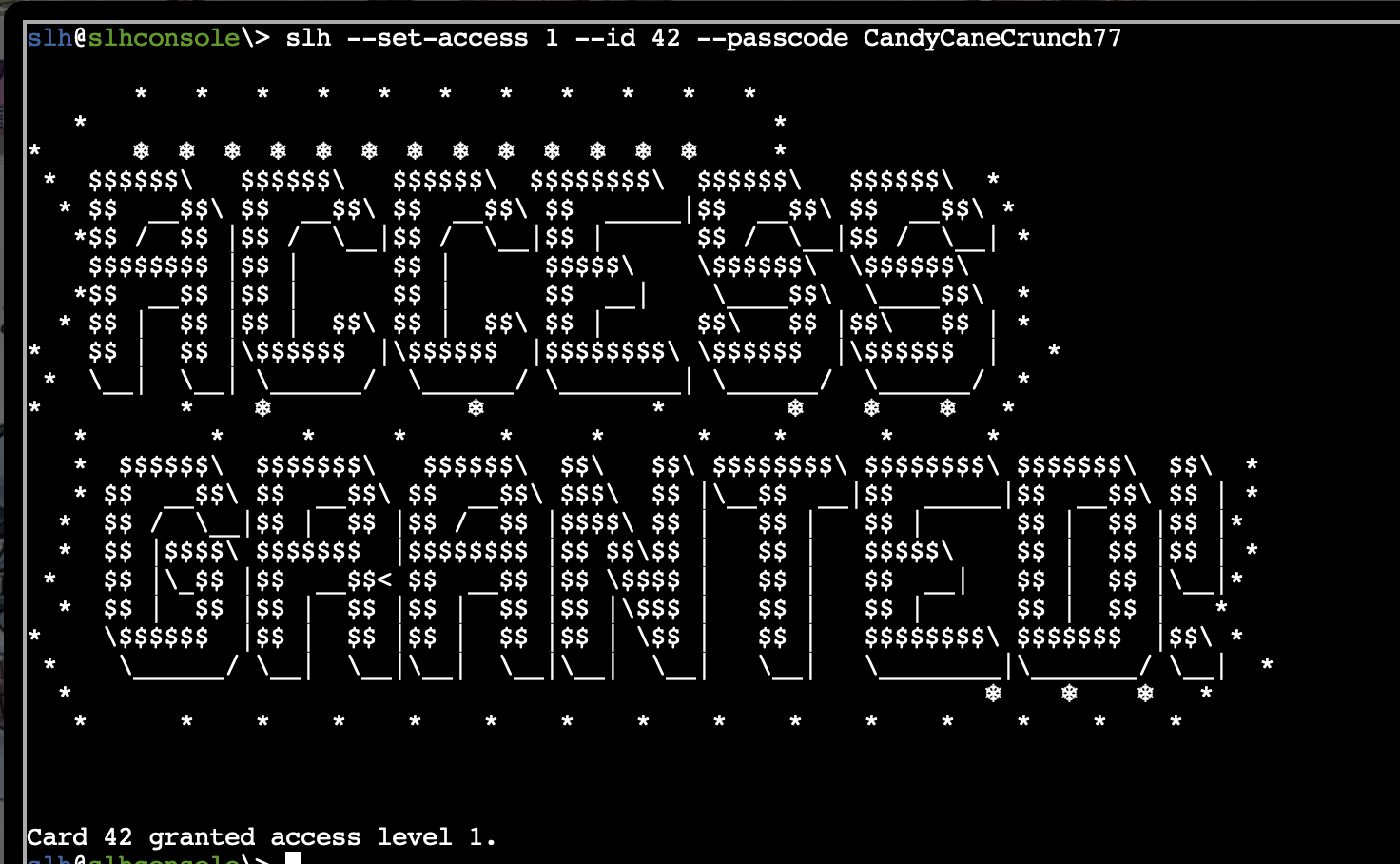
- A bit of experimentation with the SLH options gives us the appropriate command syntax.
slh --set-access 1 --id 42 --passcode CandyCaneCrunch77
- Access granted, and Silver trophy achieved.
Hardware Hacking II Gold
Jewel Loggins tells us what is needed for the gold trophy.
- An error message we might have come across earlier gives us the name of the database if we haven’t found it already.
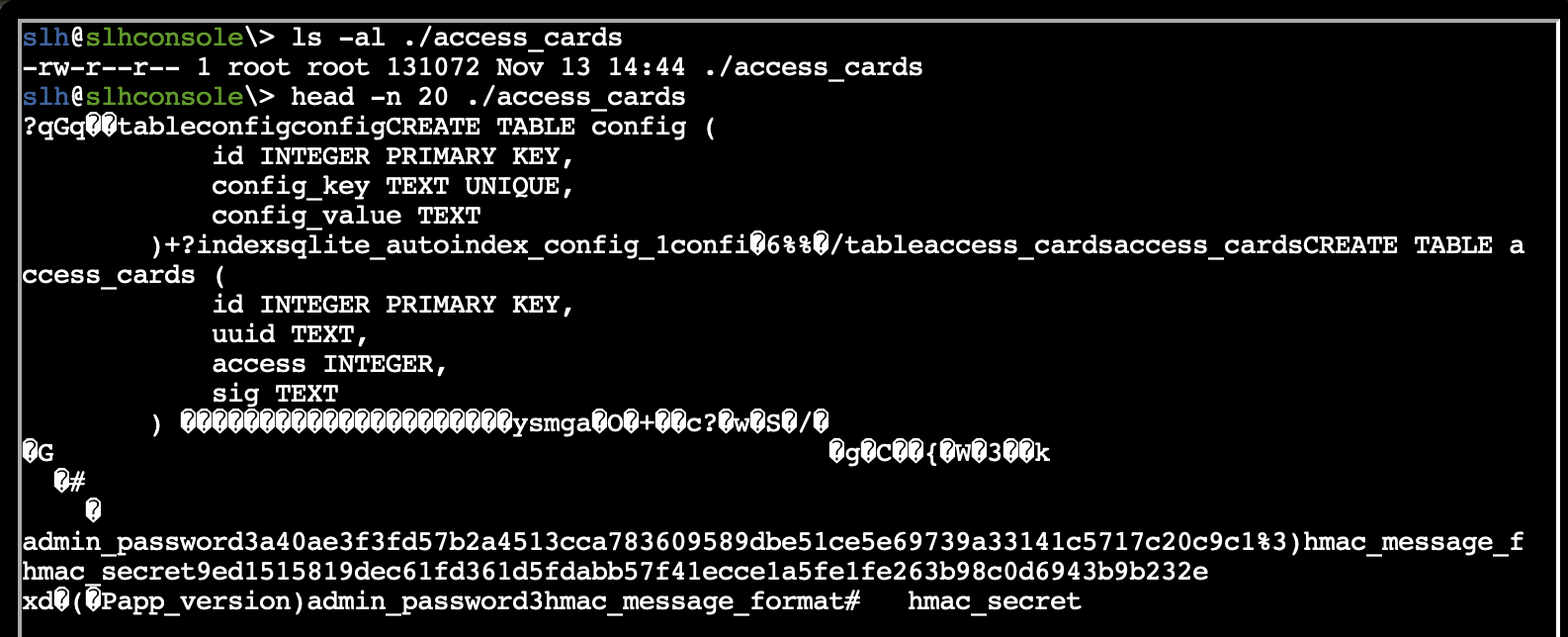
- The DB file is in our home directory and we have access to it. Examining the first several lines tells us that it’s a sqlite db, and shows us that we have some interesting credential info included in the configuration.
- Now that we know the DB type, we can examine the DB schema and pull the credentials we see.
- We know we need to work with row 42, so we can pull that as well.
sqlite> SELECT * FROM access_cards WHERE ID = 42;
42|c06018b6-5e80-4395-ab71-ae5124560189|0|ecb9de15a057305e5887502d46d434c9394f5ed7ef1a51d2930ad786b02f6ffd
- It’s easy enough to issue an update command…but that’s not enough to complete the challenge. We need to recalculate the correct digest.
- We know from the challenge dialog that the signature is an HMAC digest.
- With the information we have at this point solving the challenge with linux CLI is straightforward.
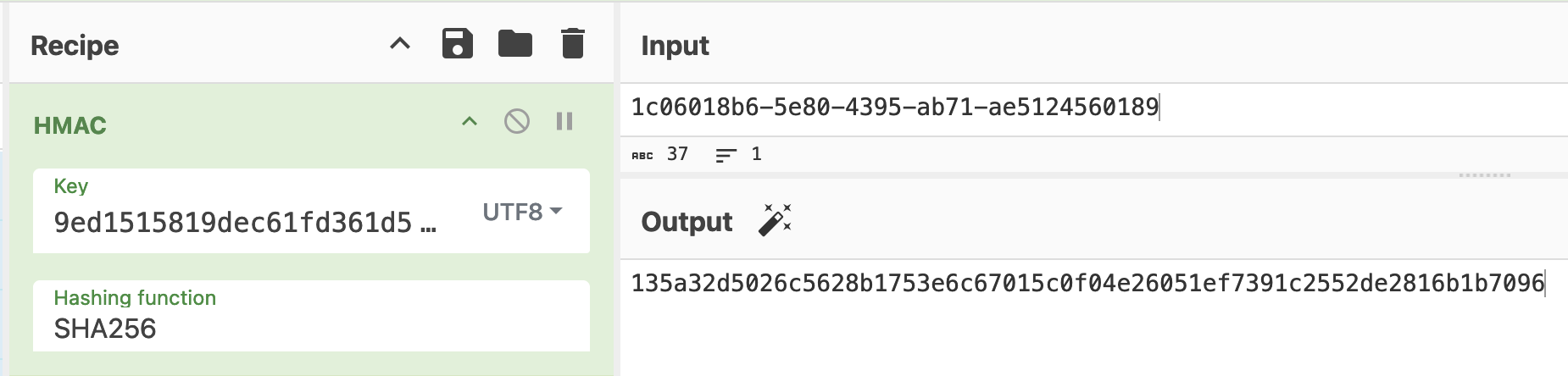
key="9ed1515819dec61fd361d5fdabb57f41ecce1a5fe1fe263b98c0d6943b9b232e"
UUID="1c06018b6-5e80-4395-ab71-ae5124560189"
echo -n "$UUID" | openssl dgst -sha256 -mac HMAC -macopt key:"$key"
- Doing this with Chef introduces a wrinkle as Chef treats the key as hex by default instead of utf-8. We need to change the key type from hex to utf-8 to use Chef for the solution.
- However we get the right digest, now that we have it we can get the Gold achievement.
sqlite3 access_cards "UPDATE access_cards SET access = 1, sig = '135a32d5026c5628b1753e6c67015c0f04e26051ef7391c2552de2816b1b7096' WHERE id = 42;"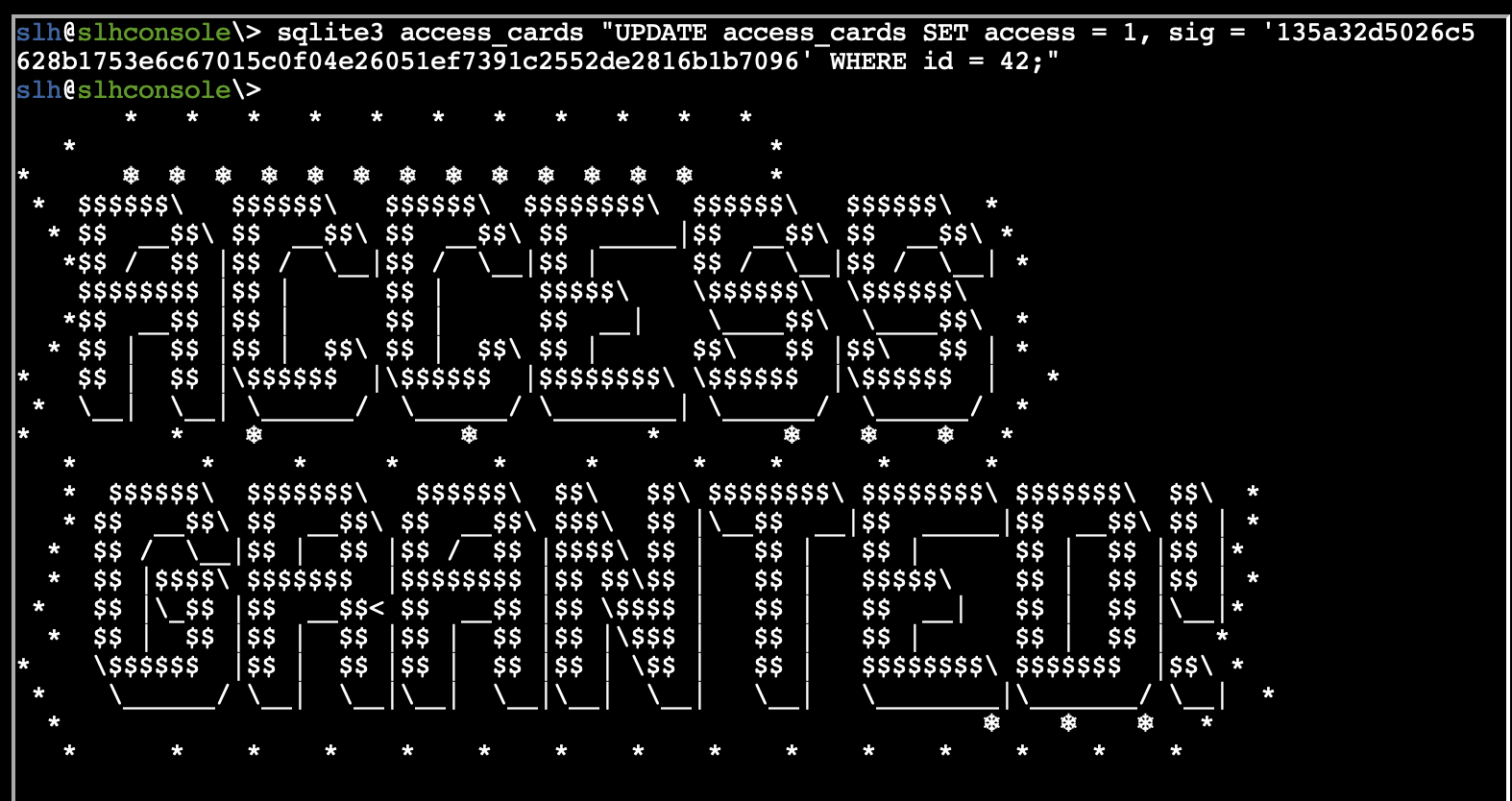
Act I is complete!